The ERMF establishes an overarching, integrated, and consistent approach to risk management firm wide.
This training will specifically focus on Operational Risk within Pillar 3 (Risk Management) of the ERMF.
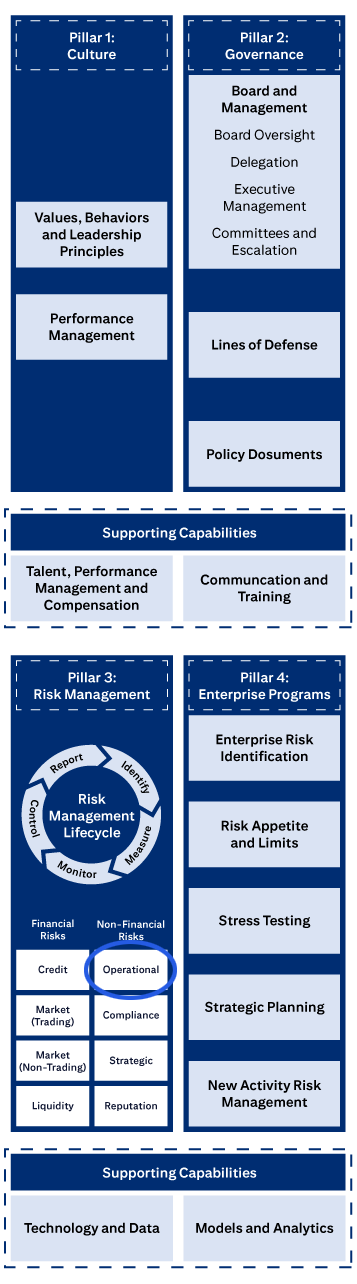
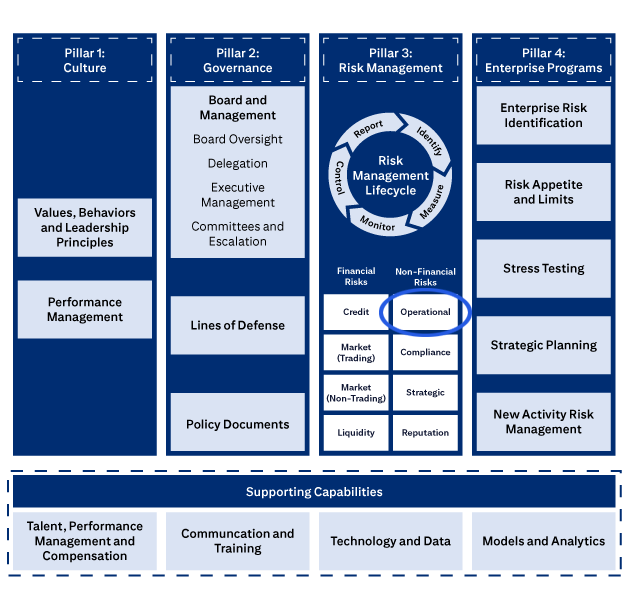

The four pillars of Citi’s ERM Framework.
Pillar 1: Culture includes Values, Behaviors and Leadership Principles, and Performance Management
Pillar 2: Governance includes Board and Management, Board Oversight, Delegation, Executive Management, Committees and Escalation, Lines of Defense, and Policies, Standards and Procedures.
Pillar 3: Risk Management covers the Risk Management Lifecycle (Identify, Measure, Monitor, Control, Report), Financial Risks (Credit, Market (Trading), Market (Non-Trading), Liquidity), and Non-Financial Risks (Operational, Compliance, Strategic, Reputation).
Pillar 4: Enterprise Programs covers Enterprise Risk Identification, Risk Appetite and Limits, Stress Testing, Strategic Planning, and New Activities Approval.
Supporting Capabilities are: Talent, Performance Management and Compensation; Communication and Training; Technology and Data; and Models and Analytics.


There are eleven sub-types of operational risk: fraud, processing, data, cyber, technology, third party, business disruption & safety, human capital, regulatory & management reporting, financial statement reporting and model risk.
Each of these are defined in full in Citi’s Risk Taxonomy which can be found here.
To proceed, select each button to reveal some examples of these risks.

Cyber Risk
Cyber Risk which relates to potential for unauthorized access, use, disclosure, modification, or destruction of information and/or disruption of information systems.

Data Risk
Data Risk which relates to the inappropriate retention, disposal, use or quality of data, or breaches of data privacy.

Fraud Risk
Fraud Risk which relates to dishonest use or intentional misappropriation of assets, resources, services or benefits for personal gain or to cause loss.

Business Disruption and Safety Risk
Business Disruption and Safety Risk which relates to physical harm to, or unavailability of, Citi premises, supporting utilities, physical assets, and/or people.


















What is Operational Risk?
Select the best response from the four options and then select Submit.
Please use the Space key only when selecting a radio option with the keyboard. The Enter key is not fully supported. If the Enter key has been used to select a radio option, please use the Escape key. Then you will be able to use the Space key again to select a radio option.
Operational Risk is best defined as: The risk of loss due to inadequate or failed internal processes, people, systems, or external events. This definition of operational risk includes legal risk - which is the risk of loss (including litigation costs, settlements, and regulatory fines) resulting from the failure of Citi to comply with laws, regulations, prudent ethical standards, and contractual obligations in any aspect of Citi's business - but excludes strategic and reputation risks.
Operational Risk is best defined as: The risk of loss due to inadequate or failed internal processes, people, systems, or external events. This definition of operational risk includes legal risk - which is the risk of loss (including litigation costs, settlements, and regulatory fines) resulting from the failure of Citi to comply with laws, regulations, prudent ethical standards, and contractual obligations in any aspect of Citi's business - but excludes strategic and reputation risks.
Operational Risk is best defined as: The risk of loss due to inadequate or failed internal processes, people, systems, or external events. This definition of operational risk includes legal risk - which is the risk of loss (including litigation costs, settlements, and regulatory fines) resulting from the failure of Citi to comply with laws, regulations, prudent ethical standards, and contractual obligations in any aspect of Citi's business - but excludes strategic and reputation risks.
That answer is correct.
Operational Risk is best defined as: The risk of loss due to inadequate or failed internal processes, people, systems, or external events. This definition of operational risk includes legal risk - which is the risk of loss (including litigation costs, settlements, and regulatory fines) resulting from the failure of Citi to comply with laws, regulations, prudent ethical standards, and contractual obligations in any aspect of Citi's business - but excludes strategic and reputation risks.
That answer is not correct.
Refer to the Understanding Operational Risk section.
That answer is not correct.
Refer to the Understanding Operational Risk section.
What is NOT an operational risk category?
Select the best response from the four options and then select Submit.
Please use the Space key only when selecting a radio option with the keyboard. The Enter key is not fully supported. If the Enter key has been used to select a radio option, please use the Escape key. Then you will be able to use the Space key again to select a radio option.
Customer/Client Protection Risk is NOT an Operational Risk Category.
Operational Risk categories include Fraud & Theft (excluding Tech), Processing Risk, Data Risk, Business Disruption and Safety Risk, Third Party Risk, Technology Risk, Cyber Risk (including Information Security), Model Risk, Human Capital Risk, Financial Statement Reporting Risk, Regulatory & Management Reporting Risk.
Customer/Client Protection Risk is NOT an Operational Risk Category.
Operational Risk categories include Fraud & Theft (excluding Tech), Processing Risk, Data Risk, Business Disruption and Safety Risk, Third Party Risk, Technology Risk, Cyber Risk (including Information Security), Model Risk, Human Capital Risk, Financial Statement Reporting Risk, Regulatory & Management Reporting Risk.
Customer/Client Protection Risk is NOT an Operational Risk Category.
Operational Risk categories include Fraud & Theft (excluding Tech), Processing Risk, Data Risk, Business Disruption and Safety Risk, Third Party Risk, Technology Risk, Cyber Risk (including Information Security), Model Risk, Human Capital Risk, Financial Statement Reporting Risk, Regulatory & Management Reporting Risk.
That answer is correct.
Customer/Client Protection Risk is NOT an Operational Risk Category.
Operational Risk categories include Fraud & Theft (excluding Tech), Processing Risk, Data Risk, Business Disruption and Safety Risk, Third Party Risk, Technology Risk, Cyber Risk (including Information Security), Model Risk, Human Capital Risk, Financial Statement Reporting Risk, Regulatory & Management Reporting Risk.
That answer is not correct.
Refer to the Understanding Operational Risk section.
That answer is not correct.
Refer to the Understanding Operational Risk section.
What can YOU do to help manage Operational Risk?
Select the best response from the four options and then select Submit.
Please use the Space key only when selecting a radio option with the keyboard. The Enter key is not fully supported. If the Enter key has been used to select a radio option, please use the Escape key. Then you will be able to use the Space key again to select a radio option.
All of the listed actions can help manage Operational Risk.
All of the listed actions can help manage Operational Risk.
All of the listed actions can help manage Operational Risk.
That answer is correct.
All of the listed actions can help manage Operational Risk.
That answer is not correct.
Refer to the following sections: Understanding Operational Risk, Implement Effective Controls and Learn from the Industry.
That answer is not correct.
Refer to the following sections: Understanding Operational Risk, Implement Effective Controls and Learn from the Industry.
Who has a role to play in managing Operational Risk at Citi?
Select the best response from the four options and then select Submit.
Please use the Space key only when selecting a radio option with the keyboard. The Enter key is not fully supported. If the Enter key has been used to select a radio option, please use the Escape key. Then you will be able to use the Space key again to select a radio option.
We can all manage risk better when we work together.
We can all manage risk better when we work together.
We can all manage risk better when we work together.
That answer is correct.
We can all manage risk better when we work together.
That answer is not correct.
Refer to the Understanding Operational Risk section.
That answer is not correct.
Refer to the Understanding Operational Risk section.
What is a potential consequence of not effectively managing Operational Risks?
Select the best response from the four options and then select Submit.
Please use the Space key only when selecting a radio option with the keyboard. The Enter key is not fully supported. If the Enter key has been used to select a radio option, please use the Escape key. Then you will be able to use the Space key again to select a radio option.
Financial losses are a potential consequence of not effectively managing Operational Risks. Other potential consequences include reputational damage and failing to meet business objectives.
Financial losses are a potential consequence of not effectively managing Operational Risks. Other potential consequences include reputational damage and failing to meet business objectives.
Financial losses are a potential consequence of not effectively managing Operational Risks. Other potential consequences include reputational damage and failing to meet business objectives.
That answer is correct.
Financial losses are a potential consequence of not effectively managing Operational Risks. Other potential consequences include reputational damage and failing to meet business objectives.
That answer is not correct.
Refer to the Understanding Operational Risk section.
That answer is not correct.
Refer to the Understanding Operational Risk section.









go to close menu button
go to close button