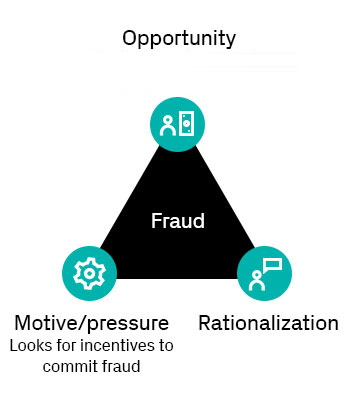
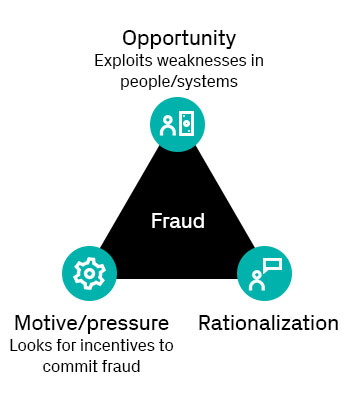
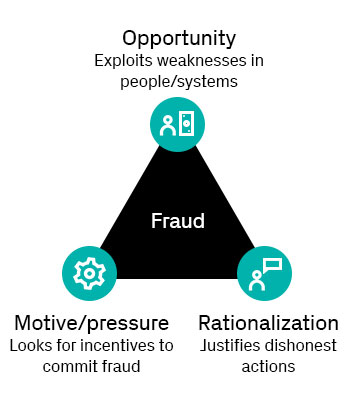
Fraud in the news
Before you delve into the course, take a look at this example.
Fraud and your responsibilities
Bad actors are now leveraging technology to gain unauthorized access to bank and client funds. Information as well as currency has become a valuable target for both internal and external fraudsters. Credit Suisse personnel must therefore be alert to ALL unusual activities and escalate any potential fraud or suspicious activity immediately.
Credit Suisse has technical controls that mitigate these risks and to further strengthen the bank-wide Anti-Fraud Framework, Anti-Fraud Global Minimum Standards (AFGMS) have been introduced in 2021 to ensure consistent and sustainable internal and external fraud risk mitigation. It is important that Credit Suisse personnel are familiar with these AFGMS as part of their day-to-day activities or whilst working on Change Initiatives.
All personnel should be aware that their footprint is monitored by the Bank. Any Credit Suisse policy violations can result in disciplinary proceedings up to termination of employment, and civil and/or criminal charges, if applicable.

About this course
This course will:
- Outline your responsibilities in escalating unusual incidents or concerns through the appropriate channels without delay
- Describe the drivers behind internal fraud
- Detail the types of internal and external fraud, and the controls we use to deter them
- Pose several scenario-based questions highlighting red flags of potential fraud
The training will take approximately 30 minutes to complete.
To register successful completion of the course, you will need to review each topic and complete the questions included throughout.
A list of useful links is available at any time by selecting the Resources button.
Intranet links might not be available over the Saba Mobile App.
Coming next
Now that you’ve had an introduction, let’s get started with your responsibilities in escalating unusual incidents or concerns, and how this should be done through the appropriate channels.
Select the Next Topic button to continue to the next topic or select the Home button to return to the home page.
Think about it...
Before we begin, take a moment to reflect.
Why is it important to escalate unusual incidents or concerns?
What is in it for you, our clients, and Credit Suisse?

What to escalate
You must escalate unusual incidents or concerns that pose, or may pose, significant risks. These include unusual incidents or concerns that could lead to financial loss for Credit Suisse or our clients.
You also must escalate unusual incidents or concerns that could cause other significant, non-financial, or reputational harm to our clients, personnel, Credit Suisse, and the integrity of the markets.

Escalation channels
When escalating an issue, you are encouraged to consider the appropriateness of the channel of escalation. You must escalate unusual incidents or concerns to any of the following parties, with the exception of incidents involving suspected violations of US Cross Border Policy (P-00025) and/or FATCA Policy (GP-00085):

|
Your primary contact to escalate unusual incidents or concerns is your line manager (except when it is inappropriate to do so) or other appropriate management or senior management. |

|
Compliance, Human Resources, General Counsel. |

|
The Credit Suisse Integrity Hotline (phone) or Integrity Line (web) (where anonymous reporting is available, if permitted by law). |
In some cases, it may be appropriate to escalate an unusual incident or concern to more than one party. For example, the operational risk aspect of a data loss incident is captured according to the Incident Collation Policy (GP-00260) and the conduct-related aspect of the incident in line with the Disciplinary Policy (GP-01058).
Coming next
Now that you have an understanding of your escalation responsibilities, let’s review the different types of internal fraud and the controls Credit Suisse uses to deter internal fraud.
Select the Next Topic button to continue to the next topic or select the Home button to return to the home page.
What is internal fraud?
Internal fraud is an intentional act committed by an organization’s own personnel to defraud the organization or the client.
Often, it is committed by one person acting alone within the Bank and can be identified through behavioral red flags displayed by fraudsters, but it can occur through the collusion between Bank personnel.
Types of internal fraud
The following types of internal fraud are common in the financial services industry:
- Unauthorized trading occurs when personnel execute trades to hide profits and losses.
- Unauthorized activity occurs when personnel transfer cash or securities from a suspense or nostro account, or depo break, or amends account statements.
- Unauthorized funds and assets transfers occur when personnel execute funds or assets transfers from client accounts without client instructions.
- Expense reimbursement fraud can be made up of mischaracterized, overstated, or fictitious expenses.

Credit Suisse controls to deter internal fraud
Credit Suisse has controls to deter internal fraud. However, even with strong controls, internal fraud can occur within the Bank.

Block leave
To mitigate the potential risks of Internal Fraud (incl. Unauthorized Trading), designated sensitive personnel under the Global Block Leave Policy (GP-00387) must take 10 consecutive business days leave period within a calendar year.
In doing so, employees must not perform duties relating to their role, access any Bank premises for business purposes, or use Bank systems including mobile applications.

Segregation of duties
This control requires additional approval or authorization for a transaction or process. The aim is to prevent domination of controls, manual override of controls, or collusion between Bank personnel.
It is imperative that there are adequate segregation of duties involving custody, authorization, and control of source documents and records.

Independent verification of authority
The independent verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
Example of internal fraud
Take a look at this example of internal fraud.
Scenario 1: Lee makes a transfer
It’s late afternoon and Lee is trying to quickly enter the last instruction from her client to transfer funds so she can leave on time for her doctor’s appointment. Under pressure, Lee does not realize that she chose the wrong beneficiary client.
Two days later, Lee receives a phone call from the client who complained that the transfer was not made in favor of the correct beneficiary.
The client demands strongly that the transaction be canceled immediately. However, as the beneficiary client does not respond to Lee’s fund return request, Lee forges transfer orders from three unrelated clients to rectify the error and gives them to her colleague Jamie, for approval.
Since Lee is a long-standing employee known for not making any errors and insisted that the orders are urgent, Jamie with no doubts about Lee’s professionalism directly approves the orders.

Did Lee and Jamie do the right thing?
Which of the following statements about Lee’s situation do you think is correct?
If you’re not sure, review the key learning points first.
Well done, that is correct. The right answer has been highlighted.
Lee should have informed her line manager about the error as soon as it was identified and recorded all details in the bank’s incident collation tool.
Jamie, to approve the order should have validated that all pre-transaction checks (identity check, authority check, authenticity check, validation of order details) were performed. In addition, Jamie should have been attentive to the red flags, e.g., payment being time-critical and needed to be processed immediately, unusual client behavior, unusual beneficiaries etc.
In addition please refer to the AFGMS ID 3 which covers the approvers’ duty which encompasses the validation of all pre-transaction checks for value changing orders.
Partially correct. The right answer has been highlighted.
Lee should have informed her line manager about the error as soon as it was identified and recorded all details in the bank’s incident collation tool.
Jamie, to approve the order should have validated that all pre-transaction checks (identity check, authority check, authenticity check, validation of order details) were performed. In addition, Jamie should have been attentive to the red flags, e.g., payment being time-critical and needed to be processed immediately, unusual client behavior, unusual beneficiaries etc.
In addition please refer to the AFGMS ID 3 which covers the approvers’ duty which encompasses the validation of all pre-transaction checks for value changing orders.
Incorrect. The right answer has been highlighted.
Lee should have informed her line manager about the error as soon as it was identified and recorded all details in the bank’s incident collation tool.
Jamie, to approve the order should have validated that all pre-transaction checks (identity check, authority check, authenticity check, validation of order details) were performed. In addition, Jamie should have been attentive to the red flags, e.g., payment being time-critical and needed to be processed immediately, unusual client behavior, unusual beneficiaries etc.
In addition please refer to the AFGMS ID 3 which covers the approvers’ duty which encompasses the validation of all pre-transaction checks for value changing orders.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
In most cases, internal fraud is committed by one person acting alone within the Bank and can be identified through suspicious behaviors, but it can occur through the collusion between Bank personnel. Suspicious behaviors include:
- Being secretive or nervous
- Unwillingness to share duties
- Willingness to override controls, often to “make things easier”
- Refusal to take vacation, or sick leave
- Accessing the Bank’s premises and/or systems during a block leave period
- Requesting to defer internal audits or inspections to “properly prepare”
- Previous history of policy breaches or near-breaches
- Unusual work hours
Examples of internal fraud include:
- Unauthorized trading occurs when personnel execute trades to hide profits and losses
- Unauthorized activity occurs when personnel transfer cash or securities from a suspense or nostro account, or depot break, or amends account statements
- Unauthorized funds and assets transfers occur when personnel execute funds or assets transfers from client accounts without client instructions
- Expense reimbursement fraud can be made up of mischaracterized, overstated, or fictitious expenses
Credit Suisse controls to deter internal fraud include:
Segregation of duties: This requires additional approval or authorization for a transaction or process. The aim is to prevent domination of controls, manual override of controls, or collusion between Bank personnel. It is imperative that there are adequate segregation of duties involving custody, authorization, and control of source documents and records.
Call-back verification: The verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
Please try again.
Unfortunately, that’s still not correct.
Review this key point before you try again.
In most cases, internal fraud is committed by one person acting alone within the Bank and can be identified through suspicious behaviors, but it can occur through the collusion between Bank personnel.
We have controls against internal fraud: block leave, segregation of duties, and call-back verification. Segregation of duties requires additional approval or authorization for a transaction or process (e.g., four-eye check principle). The aim is to prevent domination of controls, manual override of controls, or collusion between Bank personnel. It is imperative that there is adequate segregation of duties involving custody, authorization, and control of source documents and records.
Please try again.
Scenario 2: Syed examines a request

Syed a supervisor is busy approving personnel expenses for his department’s Investment Consultants.
Next on the list is Jamie’s request for reimbursement of expenses incurred for a client meeting.
Jamie requested CHF 1,000 as done for previous client meetings. However, Syed notices that Jamie was on Block Leave during this period when the client meeting occurred.
What should Syed do?
What should Syed do regarding Jamie’s request?
Please select all of the correct options. If you’re not sure, review the key learning points first.
Well done, that is correct. The right answers have been highlighted.
Jamie’s behavior is a red flag for Internal Fraud and is in violation of the Credit Suisse’s Global Block Leave Policy (GP-00387), which requires designated sensitive employees to take a leave period of 10 consecutive business days within a calendar year, and in doing so, they must not perform duties relating to their role, access any Bank premises for business purposes, or use Bank systems including mobile applications.
In addition, please refer to the AFGMS ID 17 which lists Supervisor’s responsibilities to ensure adequate oversight over internal and external fraud risks during the performance of their day-to-day responsibilities. AFGMS 21 lists the Supervisor’s responsibility to ensure adherence to the Block Leave policy and its access restrictions of their direct reports.
Partially correct. The right answers have been highlighted.
Jamie’s behavior is a red flag for potential expense reimbursement fraud, which can include mischaracterized, overstated, or fictitious expenses. Syed should request invoices and receipts from Jamie’s trip for further review. Syed should also immediately escalate the matter to line management and/or Compliance.
Incorrect. The right answers have been highlighted.
Jamie’s behavior is a red flag for potential expense reimbursement fraud, which can include mischaracterized, overstated, or fictitious expenses. Syed should request invoices and receipts from Jamie’s trip for further review. Syed should also immediately escalate the matter to line management and/or Compliance.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
In most cases, internal fraud is committed by one person acting alone within the Bank and can be identified through suspicious behaviors, but it can occur through the collusion between Bank personnel. Suspicious behaviors include:
- Being secretive or nervous
- Unwillingness to share duties
- Willingness to override controls, often to “make things easier”
- Refusal to take vacation, block leave, or sick leave
- Accessing the Bank’s premises and/or systems during a block leave period
- Requesting to defer internal audits or inspections to “properly prepare”
- Previous history of policy breaches or near-breaches
- Unusual work hours
Examples of internal fraud include:
- Unauthorized trading occurs when personnel execute trades to hide profits and losses
- Unauthorized activity occurs when personnel transfer cash or securities from a suspense or nostro account, or depot break, or amends account statements
- Unauthorized funds and assets transfers occur when personnel execute funds or assets transfers from client accounts without client instructions
- Expense reimbursement fraud can be made up of mischaracterized, overstated, or fictitious expenses
Credit Suisse controls to deter internal fraud which include:
Block Leave: To mitigate the potential risk of internal fraud, designated sensitive employees under the Global Block Leave Policy (GP-00387) must take a leave period of 10 consecutive business days within a calendar year and in doing so, employees must not perform duties relating to their role, access any Bank premises for business purposes, or use Bank systems.
Please try again and be aware that you may select more than one answer.
Unfortunately, that’s still not correct.
Review this key point before you try again.
In most cases, internal fraud is committed by one person acting alone within the Bank and can be identified through suspicious behaviors, but it can occur through collusion between Bank personnel.
We have controls against internal fraud: block leave, segregation of duties, and call-back verification. The Global Block Leave Policy (GP-00387) requires that designated sensitive employees to take a leave period of 10 consecutive business days within a calendar year, and in doing so, they must not perform duties relating to their role, access any Bank premises for business purposes, or use Bank systems including mobile applications.
Please try again and be aware that you may select more than one answer.
Coming next
You’ve worked through some examples highlighting why it’s important to have controls to deter internal fraud. Now we’ll review the different types of external fraud.
Select the Next Topic button to continue to the next topic or select the Home button to return to the home page.
What is external fraud?
External fraud consists of acts committed by clients, suppliers, or other third parties with the intention to deceive or misrepresent in order to obtain financial and/or personal gain; or with intent to deprive another of property/rights or to harm the interests of another.
Fraudulent activities conducted by third parties can create losses for Credit Suisse or our clients, undermine public and investor trust, or damage our reputation.

Types of external fraud
Types of external fraud that may affect our Bank include:
Examples of external fraud
Take a look at these examples of external fraud.

Brand misuse
A bad actor advertised a purported Credit Suisse bond investment offer on an external website, where prospective investors were asked to fill in a contact form to receive details of the offer.
A member of public, who was willing to invest in the bond, responded to the fraudulent offer and received a confirmation of agreement with transfer details such as: account number, sort code, amount to transfer; and details of a new Credit Suisse account.
There were no losses to the bank or its clients because of the Credit Suisse brand misuse, however Credit Suisse bears the reputational risks of such fraudulent activity in the market. Additionally, few members of public who invested in such fraudulent investments, believing they were investing with Credit Suisse reportedly lost their funds to such schemes.

Investment fraud
A fabricated Credit Suisse-branded bank guarantee for USD 500 million was used in a complex fraud, which targeted the USD 35 billion sovereign wealth fund of a large nation state.
The fraudsters used a complex investment fraud scheme using a purchased shell company and associated business accounts to bolster legitimacy of the investment.
Scenario 1: Martina receives a client email
Martina, a Relationship Manager receives an email from her client instructing a transfer in favor of his account to another bank.
Martina knows the client well and is aware of a call-back exception that is in place for the funds transfers instructed by the client, in favor of his account to a specific bank. Martina directly enters the payment request into the system which will be released as soon as her colleague Ava approves it.
Two days later, the client contacts Martina to understand why his account was debited when there were no instructions from him to make a transfer.
On investigation, it was revealed that the email of the client was spoofed and the IBAN (International Bank Account Number) that was credited is different than the IBAN on the call-back exception.

What type of fraud is this?
How do you best describe this scenario?
If you’re not sure, review the key learning points first.
Well done, that is correct. The right answer has been highlighted.
The email Martina received is a red flag for a cyber-enabled payment fraud, which requires deliberate deception to convince Martina as the authorized payer to execute a funds transfer without the client’s authorization. Instances of payment fraud may be cyber-enabled, using various forms of cyber fraud as a vehicle to access the funds. The call-back verification supported by security identifying questions is a control to prevent payment fraud.
In addition, please refer to the AFGMS ID 2.2 which details the pre-transaction verification checks that must be performed for all value changing orders received via non secure client communication channels.
Partially correct. The right answer has been highlighted.
The email Martina received is a red flag for a cyber-enabled payment fraud, which requires deliberate deception to convince Martina as the authorized payer to execute a funds transfer without the client’s authorization. Instances of payment fraud may be cyber-enabled, using various forms of cyber fraud as a vehicle to access the funds. The call-back verification supported by security identifying questions is a control to prevent payment fraud.
In addition, please refer to the AFGMS ID 2.2 which details the pre-transaction verification checks that must be performed for all value changing orders received via non secure client communication channels.
Incorrect. The right answer has been highlighted.
The email Martina received is a red flag for a cyber-enabled payment fraud, which requires deliberate deception to convince Martina as the authorized payer to execute a funds transfer without the client’s authorization. Instances of payment fraud may be cyber-enabled, using various forms of cyber fraud as a vehicle to access the funds. The call-back verification supported by security identifying questions is a control to prevent payment fraud.
In addition, please refer to the AFGMS ID 2.2 which details the pre-transaction verification checks that must be performed for all value changing orders received via non secure client communication channels.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter include:
Payment fraud
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds.
Cyber fraud
Cyber fraud refers to any type of deliberate deception for unfair or unlawful gain that occurs online, targeting clients and personnel. Oftentimes, cyber fraud is used to execute fraudulent disbursements of funds, securities, and confidential data or material.
Identity theft
Identity theft is a type of fraud committed using the personal non-public information of another individual without their authorization with the potential purpose of committing fraud. Identity theft poses a threat to Credit Suisse’s reputation for its due diligence and knowing whom it chooses to conduct business and for safeguarding existing client information. Identity theft is considered a crime in the United States but may be treated differently in other jurisdictions.
Please try again.
Unfortunately, that’s still not correct.
Review this key point before you try again.
The Bank and its personnel are vulnerable to external fraud risks.
Key external fraud threats you may encounter are cyber fraud, payment fraud, and identity theft.
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds. The call-back verification supported by security identifying questions is a control to prevent payment fraud.
Please try again.
What should Martina and Ava have done to prevent the fraud?
What should Martina and Ava have done to prevent the fraud?
Please select all of the correct options. If you’re not sure, review the key learning points first.
Well done, that is correct. The right answers have been highlighted.
For orders received via email, in addition to authority and authenticity checks, an identity check is required to verify the email address of the instructing party against the verified email address held on record in the relevant CS systems.
The email address must be carefully checked. Example of spoofed email addresses are below:
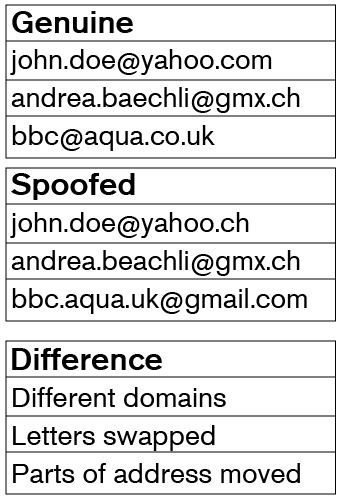
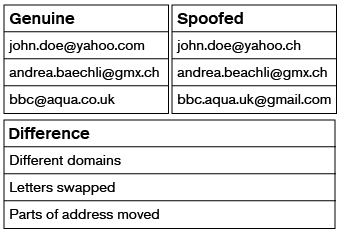

Example 1: Genuine john.doe@yahoo.com, Spoofed john.doe@yahoo.ch, Difference Different domains
Example 2: Genuine andrea.baechli@gmx.ch, Spoofed andrea.beachli@gmx.ch, Difference Letters swapped
Example 3: Genuine bbc@aqua.co.uk, Spoofed bbc.aqua.uk@gmail.com, Difference Parts of address moved
For cases where a call back exception exists, all other verification must be conducted. Furthermore, it must be carefully checked whether the IBAN number on the payment instruction fully matches precisely the IBAN number on the exception.
Partially correct. The right answers have been highlighted.
For orders received via email, in addition to authority and authenticity checks, an identity check is required to verify the email address of the instructing party against the verified email address held on record in the relevant CS systems.
The email address must be carefully checked. Example of spoofed email addresses are below:



Example 1: Genuine john.doe@yahoo.com, Spoofed john.doe@yahoo.ch, Difference Different domains
Example 2: Genuine andrea.baechli@gmx.ch, Spoofed andrea.beachli@gmx.ch, Difference Letters swapped
Example 3: Genuine bbc@aqua.co.uk, Spoofed bbc.aqua.uk@gmail.com, Difference Parts of address moved
For cases where a call back exception exists, all other verification must be conducted. Furthermore, it must be carefully checked whether the IBAN number on the payment instruction fully matches precisely the IBAN number on the exception.
Incorrect. The right answers have been highlighted.
For orders received via email, in addition to authority and authenticity checks, an identity check is required to verify the email address of the instructing party against the verified email address held on record in the relevant CS systems.
The email address must be carefully checked. Example of spoofed email addresses are below:



Example 1: Genuine john.doe@yahoo.com, Spoofed john.doe@yahoo.ch, Difference Different domains
Example 2: Genuine andrea.baechli@gmx.ch, Spoofed andrea.beachli@gmx.ch, Difference Letters swapped
Example 3: Genuine bbc@aqua.co.uk, Spoofed bbc.aqua.uk@gmail.com, Difference Parts of address moved
For cases where a call back exception exists, all other verification must be conducted. Furthermore, it must be carefully checked whether the IBAN number on the payment instruction fully matches precisely the IBAN number on the exception.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter include:
Payment fraud
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds.
Cyber fraud
Cyber fraud refers to any type of deliberate deception for unfair or unlawful gain that occurs online, targeting clients and personnel. Oftentimes, cyber fraud is used to execute fraudulent disbursements of funds, securities, and confidential data or material.
Identity theft
Identity theft is a type of fraud committed using the personal non-public information of another individual without their authorization with the potential purpose of committing fraud. Identity theft poses a threat to Credit Suisse’s reputation for its due diligence and knowing whom it chooses to conduct business and for safeguarding existing client information. Identity theft is considered a crime in the United States but may be treated differently in other jurisdictions.
Please try again and be aware that you may select more than one answer.
Unfortunately, that’s still not correct.
Review this key point before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter are cyber fraud, payment fraud, and identity theft.
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds. The call-back verification supported by security identifying questions is a control to prevent payment fraud.
For cases where a call back exception exists, all other verification must be conducted. Furthermore, it must be carefully checked whether the IBAN number on the payment instruction fully matches the IBAN number on the exception.
Please try again and be aware that you may select more than one answer.
Scenario 2: Rahul performs a fraud risk assessment

To move towards a more sustainable global economy, the bank decides to introduce a carbon offsetting compensation program for clients financed for the purchase of yachts or aircrafts. The bank under this program will arrange the purchase of emission reduction certificates to offset the emissions caused by their aircrafts or yachts.
The team of Rahul will administer the compensation process from the calculation of the CO2 emissions based on the information provided by the aircraft’s operator, to the purchase of the certificates from selected and approved vendors, and to the recharge it back to the clients. From the sales proceeds of the certificates, the vendors will use it to finance projects around the world that reduce carbon emissions, protect biodiversity, and / bring benefits to local communities (Green projects).
As part of the New Business review and following AFGMS requirements, Rahul is asked to perform a fraud risk assessment with respect to the carbon compensation program in aviation financing.
What should Rahul do?
Rahul asks you for help in identifying external fraud scenarios related to this programme.
Please select all of the correct options. If you’re not sure, review the key learning points first.
Well done, that is correct. The right answers have been highlighted.
The carbon offsetting compensation program can present external fraud opportunities which will need to be addressed by the implementation of compensating controls:
- The client can encourage the aircraft’s operator to underestimate the flight hours to help him reduce the cost to offset the client’s carbon emissions.
- The vendors could not follow through on their commitments and retain the sales’ proceeds of the certificates for themselves.
- Bad actors could impersonate the vendors and send invoices with fraudulent payment details.
Also refer to the AFGMS ID 24 which requests the performance of a fraud risk assessment in case of new or changed processes / tools / products / services.
Partially correct. The right answers have been highlighted.
An unsupported leap in profits may indicate financial statement fraud, which Rahul should immediately escalate to his line manager or Compliance for further investigation.
Incorrect. The right answers have been highlighted.
An unsupported leap in profits may indicate financial statement fraud, which Rahul should immediately escalate to his line manager or Compliance for further investigation.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter include:
Financial statement fraud
Financial statement fraud occurs where a client provides falsified documentation to misrepresent his or her assets and/or revenues to obtain products and services from the Bank. Examples of financial statement fraud schemes include recording of fictitious revenue or in improper account periods, improper disclosures, or concealment of liabilities.
Investment fraud
The typical investment fraud schemes are characterized by offers of low- or no-risk investments, guaranteed returns, overly consistent returns, complex strategies, or unregistered securities. Examples of investment fraud may include Ponzi schemes, pyramid schemes and a request to pay a processing fee in order to invest.
Credit Suisse brand misuse
Credit Suisse brand misuse refers to a fraud scheme which may involve falsified documents, fraudulent websites and e-mail accounts misusing the Credit Suisse brand or logo. The intention is to make the documents appear as a legitimate investment or financial product to potential investors, banks, or consumers so they invest in the fraud scheme.
Please try again and be aware that you may select more than one answer.
Unfortunately, that’s still not correct.
Review this key point before you try again.
The Bank and its personnel are vulnerable to external fraud risks.
Key external fraud threats you may encounter are vendor and supplier fraud, payment fraud, and financial statement fraud.
Fraud committed by clients or parties close to clients are considered as external fraud which are usually committed through the provision of falsified information or documentation.
Please try again and be aware that you may select more than one answer.
Coming next
Now that you’ve worked your way through examples of internal and external fraud, let’s look at one final scenario.
Select the Next Topic button to continue to the next topic or select the Home button to return to the home page.
Scenario: Jessie receives a payment instruction

It’s a day before the close on a purchase loan from a client, Jessie who works in the Trade Management team receives an email from the client, instructing to change the Standing Settlement Instructions (“SSI”) to a new financial institution to which the proceeds are to be wired.
As the revised SSI is not in the system, Jessie sends the revised instructions to the Operations team to set-up a new SSI.
Scenario: Lita performs a call-back
Lita who works in the Operations team receives the instructions from Jessie. A call-back must be performed to confirm the authenticity of the new instructions to set-up a new SSI.
Lita follows its procedure and calls the client's switchboard number, which was unsuccessful due to the current work from home situation in the pandemic.
As a result, and on the instructions of Jessie, Lita moves to a Direct Call-back procedure and calls the phone number listed on the email signature of the client. The call back was successful this time and the payment was processed per the revised SSI.
A few days later the client contacts Jessie inquiring about payment of the funds which was still not received. Upon investigation it was discovered that the client's email account had been hacked and that the instruction to change the SSI was fraudulent. Using the client's email domain, the fraudster was able to send the fraudulent payment instructions to Jessie purporting to be the client and bypassing the call-back control.

What should Lita have done to prevent the fraudulent payment?
What should Lita do?
If you’re not sure, review the key learning points first.
Well done, that is correct. The right answer has been highlighted.
The verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
The call back should not be performed on a phone number received / obtained via an unsecured channel such as email.
Partially correct. The right answer has been highlighted.
The verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
The call back should not be performed on a phone number received / obtained via an unsecured channel such as email.
Incorrect. The right answer has been highlighted.
The verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
The call back should not be performed on a phone number received / obtained via an unsecured channel such as email.
Unfortunately, that’s incorrect.
Take a moment to review these key points before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter include:
Payment fraud
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds.
Cyber fraud
Cyber fraud refers to any type of deliberate deception for unfair or unlawful gain that occurs online, targeting clients and personnel. Oftentimes, cyber fraud is used to execute fraudulent disbursements of funds, securities, and confidential data or material.
Identity theft
Identity theft is a type of fraud committed using the personal non-public information of another individual without their authorization with the potential purpose of committing fraud. Identity theft poses a threat to Credit Suisse’s reputation for its due diligence and knowing whom it chooses to conduct business and for safeguarding existing client information. Identity theft is considered a crime in the United States but may be treated differently in other jurisdictions.
Please try again.
Unfortunately, that’s still not correct.
Review this key point before you try again.
The Bank and its personnel are vulnerable to external fraud risks. Key external fraud threats you may encounter are cyber fraud, payment fraud, and identity theft.
Payment fraud is a result of a deliberate deception to convince the authorized payer to execute a payment without client authorization. Cyber-enabled payment fraud uses various forms of cyber fraud as a vehicle to access the funds. The verification of authority for e.g., via call-back or transaction signing is used to verify transfer of funds/assets (i.e., payments, securities) or requests for changes to client or vendor static data. For such requests, an identity check of the instructing party; an authority check i.e., the right to move funds/assets or changes to client/vendor static data and authenticity checks must be performed to determine legitimacy of the instruction details. For further information please refer to the AFGMS.
For cases where a call back cannot be performed, the payment must be put on hold and escalated to the Line Manager / Compliance officer for further guidance.
Please try again.
Let’s recap
Before we conclude, take a moment to reflect on the scenarios you encountered throughout the course.
In summary
Here is a summary of the key points covered in the course.
You can also download and print the Escalation and Identifying Potential Fraud Course Summary.
Conclusion
You have completed this course and can now close the module and exit.